Do you want to: Ask a how-to question
DocSpace version:
Gestione documentale:
[ ONLYOFFICE DocSpace ]
v.2.5.1
Editor online:
[ ONLYOFFICE Docs ]
v.8.1.0.169
Type of installation of the DocSpace (deb/rpm, exe, installation step from documentation):
OS:
Browser version: chrome
Additional information:
Good morning,
we installed onlyoffice docspace enterprise version via deb packages.
We have communication configuration problems between docspace and onlyoffice document.
Docspace and document will need to be configured behind an nginx reverse proxy. Both docspace and document are installed onpremise (package installation using docspace-install.sh) on the same server. We defined the reverse configuration for docspace as follows,
HTTPS server
server {
listen 443 ssl;
server_name docspace.regione.abruzzo.it;
access_log /var/log/nginx/docspace.regione.abruzzo.it.access.log main;
error_log /var/log/nginx/docspace.regione.abruzzo.it.error.log;
ssl_certificate /etc/nginx/ssl/certs/regione.abruzzo.it.crt;
ssl_certificate_key /etc/nginx/ssl/private/regione.abruzzo.it.key;
ssl_session_timeout 1440m; ### = 1d
ssl_session_timeout 5m;
ssl_session_cache shared:le_nginx_SSL:1m;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
ssl_prefer_server_ciphers on;
# disable any limits to avoid HTTP 413 for large image uploads
#client_max_body_size 0;
client_max_body_size 2000M;
# required to avoid HTTP 411: see Issue #1486 (https://github.com/moby/moby/issues/1486)
chunked_transfer_encoding on;
location / {
proxy_pass http://x.y.z.t;
add_header X-Served-By $host;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-Scheme $scheme;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
}
}
while the document configuration we took the configuration as per the documentation.
This is documentation server config in nginx reverse proxy
Use this example for proxy HTTPS traffic to the document server running at ‘backendserver-address’.
Replace {{SSL_CERTIFICATE_PATH}} with the path to the ssl certificate file
Replace {{SSL_KEY_PATH}} with the path to the ssl private key file
upstream docservice {
server x.y.z.t:8083;
}
map $http_host $this_host {
“” $host;
default $http_host;
}
map $http_x_forwarded_proto $the_scheme {
default $http_x_forwarded_proto;
“” $scheme;
}
map $http_x_forwarded_host $the_host {
default $http_x_forwarded_host;
“” $this_host;
}
map $http_upgrade $proxy_connection {
default upgrade;
“” close;
}
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $proxy_connection;
proxy_set_header X-Forwarded-Host $the_host;
proxy_set_header X-Forwarded-Proto $the_scheme;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
Normal HTTP host
server {
listen 0.0.0.0:80;
listen [::]:80 default_server;
server_name documentserver.regione.abruzzo.it;
server_tokens off;
Redirects all traffic to the HTTPS host
return 301 https://$server_name:443$request_uri;
}
server {
listen 0.0.0.0:443 ssl;
listen [::]:443 ssl default_server;
server_tokens off;
root /usr/share/nginx/html;
server_name documentserver.regione.abruzzo.it;
Strong SSL Security
Strong SSL Security on nginx - Raymii.org
access_log /var/log/nginx/documentserver.regione.abruzzo.it.access.log main;
error_log /var/log/nginx/documentserver.regione.abruzzo.it.error.log;
ssl_certificate /etc/nginx/ssl/certs/regione.abruzzo.it.crt;
ssl_certificate_key /etc/nginx/ssl/private/regione.abruzzo.it.key;
ssl_verify_client off;
ssl_ciphers “EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH”;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_prefer_server_ciphers on;
[Optional] Before enabling Strict-Transport-Security headers, ensure your server is properly configured for SSL.
This directive informs the browser to always use HTTPS. For more info see:
- Strict-Transport-Security - HTTP | MDN
add_header Strict-Transport-Security “max-age=31536000; includeSubDomains” always;
add_header X-Frame-Options SAMEORIGIN;
add_header X-Content-Type-Options nosniff;
[Optional] If your certficate has OCSP, enable OCSP stapling to reduce the overhead and latency of running SSL.
Replace with your ssl_trusted_certificate. For more info see:
- https://medium.com/devops-programming/4445f4862461
- SSL OCSP stapling won't enable - NGINX - Ruby-Forum
- How To Configure OCSP Stapling on Apache and Nginx | DigitalOcean
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/nginx/ssl/stapling.trusted.crt;
resolver 208.67.222.222 208.67.222.220 valid=300s; # Can change to your DNS resolver if desired
resolver_timeout 10s;
[Optional] Generate a stronger DHE parameter:
cd /etc/ssl/certs
sudo openssl dhparam -out dhparam.pem 4096
ssl_dhparam /etc/ssl/certs/dhparam.pem;
location / {
proxy_pass http://docservice;
proxy_http_version 1.1;
}
}
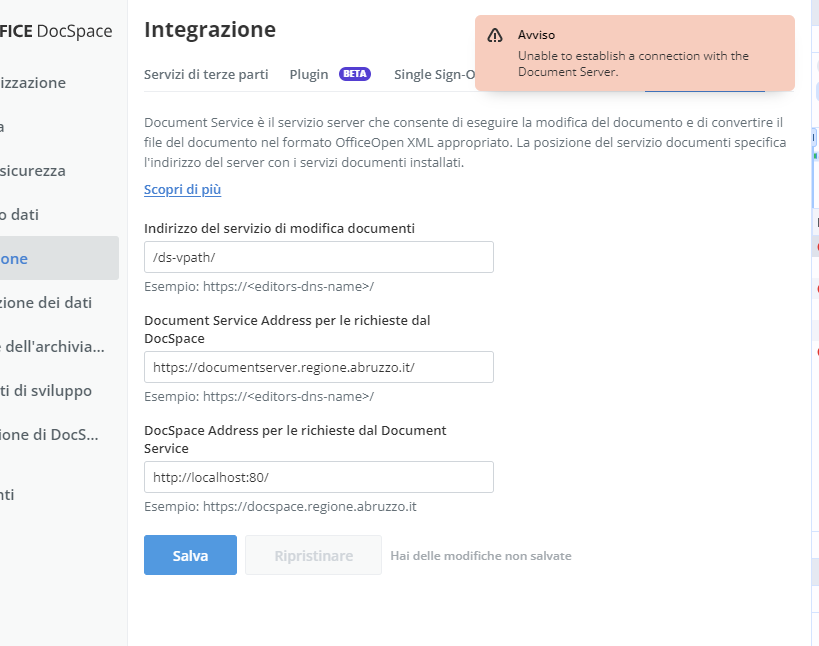
Both docspace and document are configured in http and the https part is on the nginx reverse proxy (ngix reverse is the SSL termination). We have several problems. The first is that we are unable to configure the document service on docspace and we receive the following error.
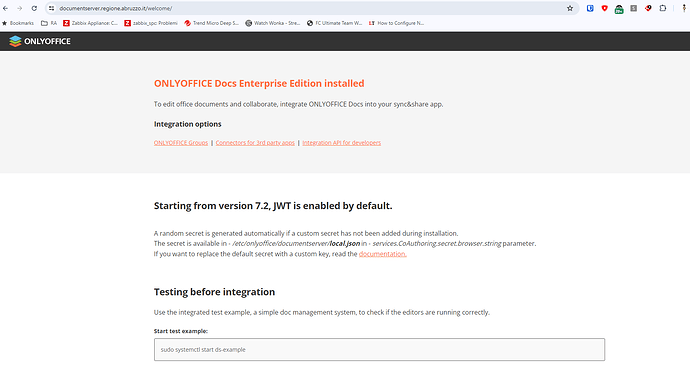
but documentserver working with fqdn
Have we made any mistakes on the reverse side configuration? is there any further configuration to do on the docspace side?